The attack surface on vehicles is increasing exponentially as cars become more connected and self-driving features have been added through artificial intelligence. All of those features bring many benefits to us, including safety, but from a cyber security perspective, they also bring some risks. In this post, we will showcase hacking car key fob frequency.
I will show you how to hack wireless signals to open car doors using Software-Defined Radio (SDR). The same technique works for other devices, such as remote controls, garage doors, and wireless doorbells.
As we focus on car hacking, let’s jump directly to our target device: key fobs.
Renault Fuego introduced them to the market in 1992, using an RFID signal – Radio Frequency Identification – and they became very popular in 1995.
Exploring Car Key Fob Vulnerabilities
The key-fob frequency scanner app uses a transponder that transmits a signal to the vehicle to lock/unlock the car door or even start the vehicle. The signal communicates with an immobilizer, preventing it from accepting the key-fob command unless it receives the correct code or token.

Older key fobs used static codes to lock/unlock the door. Every time you pressed the button, the same code was generated. Now, cars are using a rolling code or challenge-response system to become more secure. Every time you press the button, a new code is generated, and the immobilizer is expecting a specific code as they’re both synced
This can prevent simple record & replay attacks that could be used on old key-fob systems, but they are also not perfect. There are ways to bypass this security feature.
What You Will Need for This Exercise
-
- An SDR Device
-
- System running Linux, preferably
-
- Gqrx
-
- Gnu Radio Companion
There are several options for the SDR device, from the cheapest $20 RTL-SDR device to more powerful and sophisticated devices like the one from Ettus Research, which costs $2,000.
Another good option is the HackRF One, which costs around $400. The differences between them are the following:
-
- Price
-
- Only Receives Signals
-
- Both Transmit and Receives Signals
-
- Sample Rate
-
- Processor Speed
-
- Others
Now, let’s analyze the radio signal between the key fob and the vehicle. I’m using a HackRF One for this.

Key Fobs operate on a standard frequency of ˜315MHz in the US and 433MHz in Europe. But let’s say we don’t know it. There are basically two ways to determine it. One way is to use a Spectrum Analyzer to identify the signal and its frequency. In this particular case, I used a frequency scanner app called gqrx.
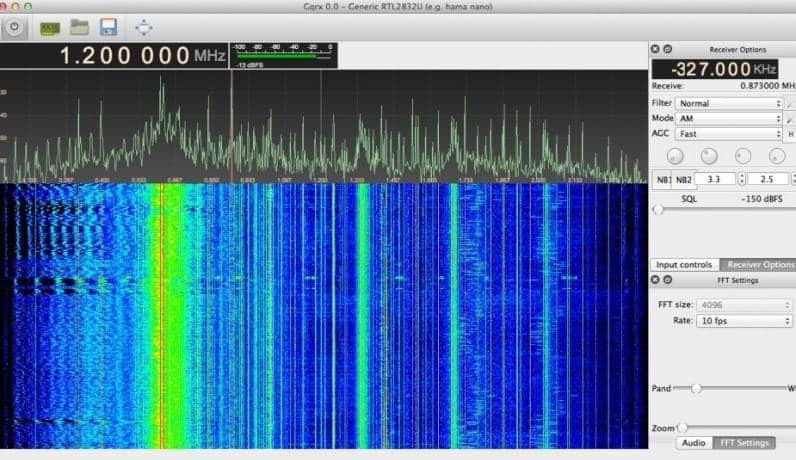
Another way is to use the FCC Website. All wireless signals must be licensed by the FCC, and you can find a lot of good information on the FCC website, including not only the frequency the device operates on but also schematics, internal and external pictures, and other useful information.
From there, you can open your GNU radio companion application using a similar flow I used to listen to the radio signal while pressing the key fob button and save the data to a file.
Then, you can use a different flow from GNU Radio Companion to transmit the recorded data through your SDR device (in my case, the HackRF One).
This simple method allows you to open car doors using old key fobs, insecure garage doors, and many other things. But as I mentioned before, newer key fobs use a rolling code, and in order to hack it or bypass it, you have a couple of options:
-
- Pulling Response Code from Memory
-
- Brute Forcing
-
- Forward Prediction Attacks
-
- Dictionary Attacks
-
- Jamming
Jamming is the most common method used. It adds noise/jamming to the signal while at the same time recording the original code from your key fob. If the noise is strong enough, it will prevent the immobilizer from understanding the signal generated. Now, you have one valid code stored that has not been used yet, and if you replay that code, you’ll be able to open your car door.

For more information, also check the video of this post on our YouTube Channel below, and don’t forget to subscribe to our channel.

