Phishing remains one of the top attack vectors in cyber security, posing significant threats to individuals and organizations. As security professionals, understanding how email works and the mechanisms to protect against phishing attacks is crucial. This blog covers email security, explains how emails work, and explores critical email authentication protocols such as DKIM, SPF, and DMARC to enhance our defenses against phishing.
The Basics of Email
Email is a ubiquitous form of communication in the digital age, with billions of messages sent daily. Despite its widespread use, many users do not fully understand an email’s journey from the sender to the recipient. This lack of knowledge can make it easier for attackers to exploit email
vulnerabilities.
Email Architecture
Emails are sent usin
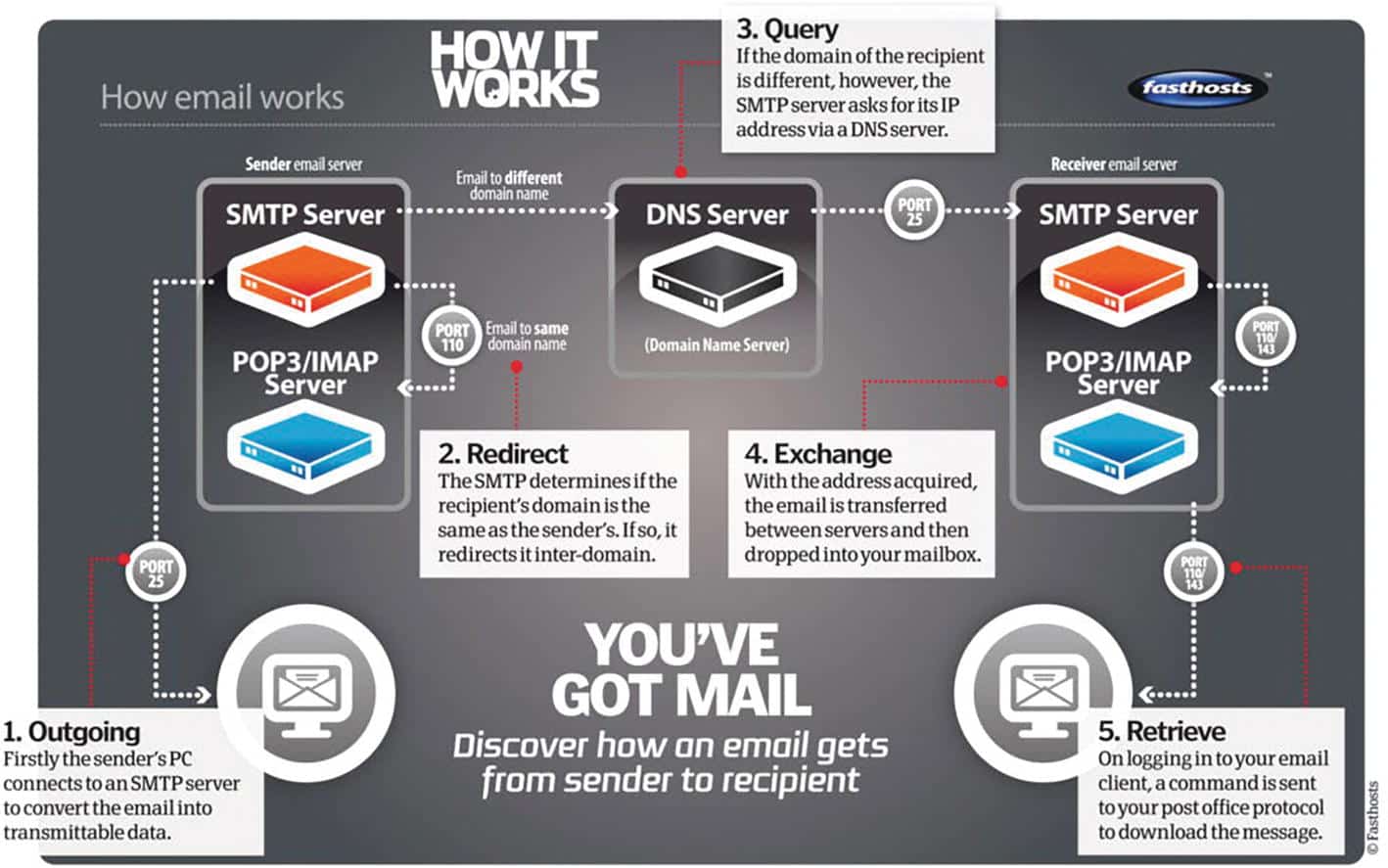
g email clients, such as desktop applications (like Microsoft Outlook) or web applications (like Gmail). Regardless of the client, the process of sending an email follows a similar path involving several key steps and components:
Email Composition: The sender creates an email message, including the recipient’s address, subject, and body content.
SMTP Server: The email is first sent to the sender’s SMTP (Simple Mail Transfer Protocol) server.
DNS Resolution: If the recipient’s domain differs from the sender’s, the SMTP server uses a DNS (Domain Name System) server to resolve the recipient’s domain to an IP address.
Recipient’s SMTP Server: The email is forwarded to the recipient’s SMTP server.
POP3/IMAP Server: The recipient’s SMTP server sends the email to a POP3 or IMAP server,
where it waits for the recipient to retrieveit.
This journey involves multiple network devices and servers, making it essential to secure each step to prevent malicious activities such as phishing.
Email Authentication Protocols
Several email authentication protocols have been developed to combat phishing and other email-based attacks. These protocols help verify that the email is from the purported sender and has not been tampered with during transit.
DKIM (DomainKeys Identified Mail)
DKIM is an email authentication method designed to detect forged sender addresses in emails, a common tactic in phishing attacks. It uses cryptographic signatures to verify the authenticity of the email’s origin.
- How DKIM Works:
- Signing: The sending mail server generates a cryptographic signature for the email, which is added to the email header.
- Verification: The recipient’s mail server retrieves the public key from the sender’s DNS records and uses it to verify the signature.
A valid DKIM signature confirms that the email was sent from the claimed domain and its content has not been altered.
SPF (Sender Policy Framework)
SPF is another email authentication protocol that helps prevent spam by specifying which mail servers are authorized to send emails on behalf of a domain.
- How SPF Works:
- DNS Record: The domain owner publishes an SPF record in their DNS, listing the IP addresses of authorized mail servers.
- Validation: When receiving an email, the recipient’s mail server checks the SPF record to ensure the sending server’s IP address is authorized.
The email may be flagged as suspicious or rejected if the sending server’s IP address is not listed in the SPF record.
DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds on DKIM and SPF by providing a mechanism for domain owners to specify how unauthenticated emails should be handled and to receive reports on email authentication results.
- How DMARC Works:
- Policy Declaration: The domain owner publishes a DMARC policy in their DNS, specifying the actions to take (e.g., quarantine or reject) if an email fails DKIM or SPF checks.
- Alignment: DMARC requires that the domain in the “From” header matches the domains used in DKIM and SPF checks.
- Reporting: DMARC enables domain owners to receive reports on authentication results, helping them monitor and improve their email security.
DMARC significantly enhances email security by ensuring that emails failing DKIM and SPF checks are appropriately handled and reported.
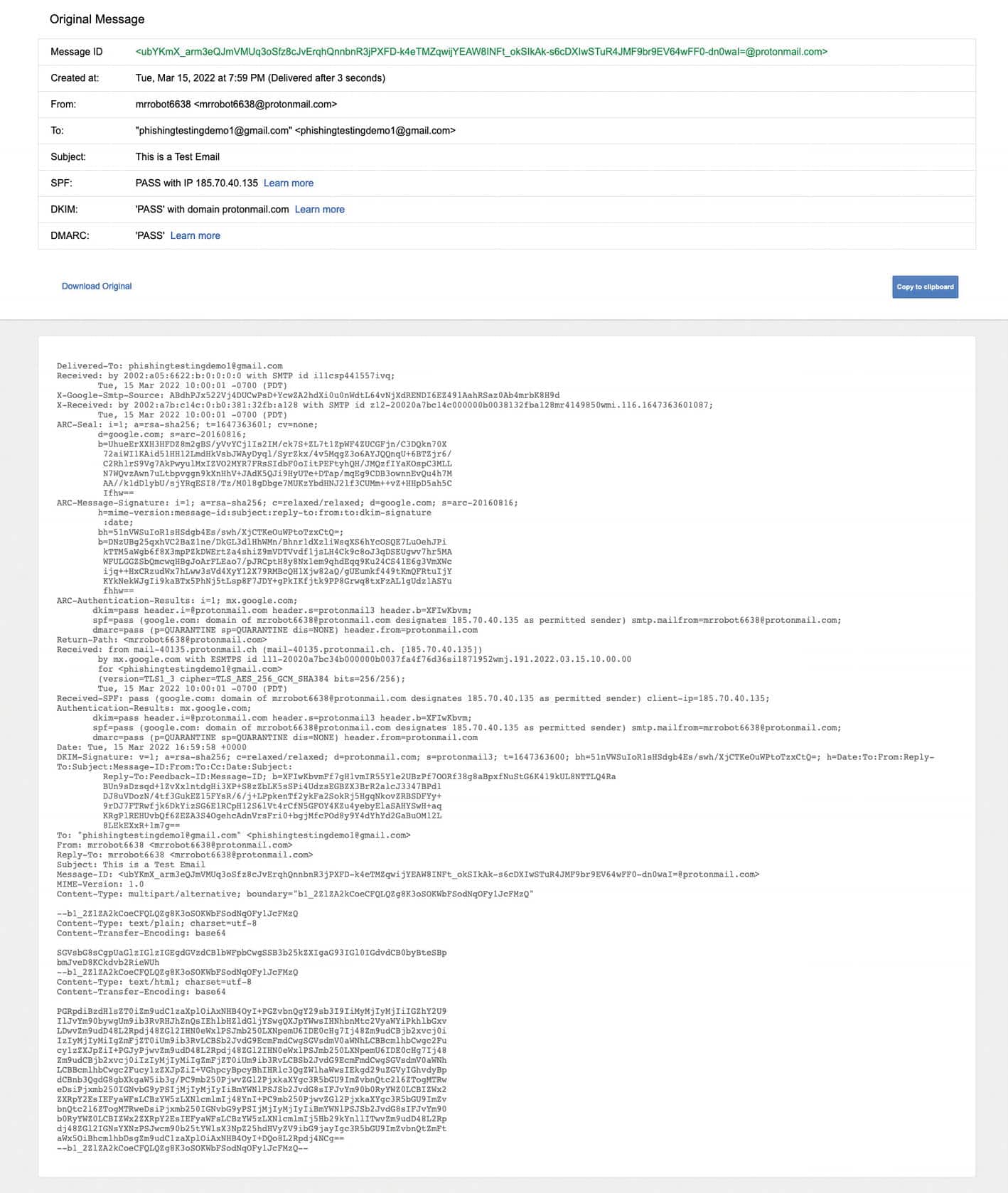 Gmail Email Header
Gmail Email Header
Practical Steps to Implement Email Authentication
Implementing DKIM, SPF, and DMARC requires email administrators and domain owners to coordinate. Here are the practical steps to set up these protocols:
Setting Up DKIM
- Generate DKIM Keys: Generate a public-private key pair.
- Publish Public Key: Add the public key to the domain’s DNS records.
- Configure Mail Server: Configure the mail server to sign outgoing emails with the private key.
Setting Up SPF
- Create SPF Record: Define the IP addresses of authorized mail servers in an SPF record.
- Publish SPF Record: Add the SPF record to the domain’s DNS.
Setting Up DMARC
- Create a DMARC Policy: Define the desired policy (e.g., none, quarantine, reject) and the email addresses used to receive reports.
- Publish DMARC Record: Add the DMARC record to the domain’s DNS.
Monitoring and Maintenance
- Regular Audits: Review DKIM, SPF, and DMARC configurations to ensure they are up-to-date.
- Report Analysis: Analyze DMARC reports to identify and mitigate unauthorized email activity.
Conclusion
Phishing remains a prevalent threat, but security professionals can significantly enhance their defenses by understanding email’s inner workings and implementing robust email authentication protocols like DKIM, SPF, and DMARC. These measures protect against phishing and help maintain the integrity and trustworthiness of email communications.
Stay vigilant, educate your users, and continuously improve your email security posture to stay ahead of malicious actors. For more cybersecurity tips and tutorials, visit LufSec and subscribe to our blog for the latest updates and insights. Also, visit our YouTube Channel.
Don’t forget to check our online courses!
