Welcome to our comprehensive guide on AWS security. As businesses increasingly shift their operations to the cloud, understanding the intricacies of AWS security becomes paramount. This blog post will explore the shared responsibility model and best practices for ensuring a robust security posture in AWS environments.
The Importance of Cloud Security
In today’s digital era, cloud security is critical for safeguarding data and maintaining business integrity. Cloud computing offers unparalleled scalability, agility, and cost efficiency but also brings unique security challenges. Trusting third-party providers like AWS with sensitive data and operations underscores the need for robust security measures.
The AWS Shared Responsibility Model
A key concept in AWS security is the shared responsibility model, which delineates the security obligations of AWS and its customers. This model is crucial for understanding how to secure your AWS environment effectively.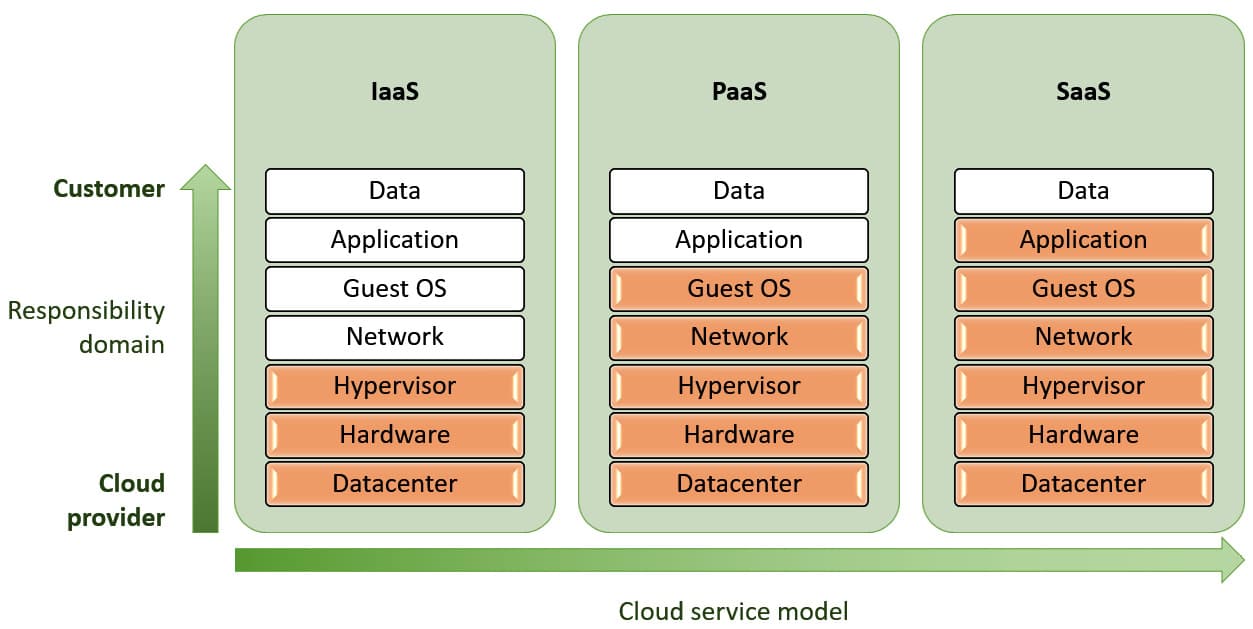
Security “Of” the Cloud
AWS is responsible for securing the underlying infrastructure, including hardware, software, networking, and facilities that run AWS services. This encompasses physical security, server infrastructure, and network and virtualization security.
Security “In” the Cloud
Customers are responsible for securing their data, applications, operating systems, and networks within the AWS environment. This includes managing user access, encrypting data, and configuring AWS services securely.
Navigating Cloud Security Challenges
Complexity
AWS offers over 200 fully featured services, each with unique configurations and security considerations. The cloud’s dynamic, scalable nature adds layers of complexity, making it essential to understand and manage these environments effectively.
Visibility and Control
Maintaining visibility and control in the cloud requires a different approach than traditional on-premises environments. AWS provides tools like AWS CloudTrail, AWS Config, and AWS Security Hub to enhance visibility and control, enabling detailed monitoring and centralized security alerting.
AWS Security Best Practices
Implementing AWS security best practices is vital for protecting your resources, data, and applications. Here are some fundamental guidelines:
Understand the Shared Responsibility Model
A thorough understanding of the shared responsibility model is essential. AWS secures the cloud infrastructure, while customers are responsible for securing their data and applications within the cloud.
Use AWS Security Services and Features
Leverage AWS security services such as Amazon GuardDuty for threat detection, AWS Security Hub for security posture management, and AWS Config to monitor resource configurations continuously. These services form the backbone of AWS security.
Develop a Strong Identity and Access Management Strategy
Implement robust identity and access management (IAM) policies. AWS IAM allows you to create users, groups, and roles with specific permissions, adhering to the principle of least privilege to minimize potential risks.
Protect Your Data
Data protection involves classification, encryption, and secure handling practices. For encryption, use services like AWS Key Management Service (KMS) and AWS Certificate Manager, and implement secure data storage and backup procedures.
Ensure Network Security
Define your Virtual Private Cloud (VPC) and subnets strategically to enhance security. Use security groups, network access control lists (NACLs), and AWS Network Firewall to protect your resources from threats.
Integrate Security into Your Development Lifecycle
Adopt DevSecOps practices to integrate security into the development lifecycle. Shift security left by addressing issues early in development, automating security tasks, and continuously monitoring and improving your security posture.
Monitoring and Auditing
Effective monitoring and auditing are crucial for detecting and responding to security incidents. AWS CloudTrail provides governance, compliance, and operational monitoring, while Amazon CloudWatch enables metric collection and log monitoring for a comprehensive view of your environment’s health.
Continuous Improvement
Security is an ongoing process. Stay informed about the latest AWS security features, threats, and mitigation techniques. Regularly review and update your security settings and configurations to adapt to evolving threats and changes in your AWS environment.
Conclusion
Understanding AWS security and the shared responsibility model is crucial for protecting your cloud environment. You can build and maintain a robust security posture by implementing best practices and leveraging AWS security tools. Stay proactive, continuously monitor, and adapt to secure your AWS environment.
For more insights and detailed guidance on AWS security, visit our YouTube Channel and explore our range of cybersecurity resources and services.



