GitHub is still in the throes of a massive DDoS attack which has blighted the site since Thursday. While the origins of and reasons for the attack is not yet fully known, the fact that two projects relating to Chinese anti-censorship have been targeted speaks volumes.
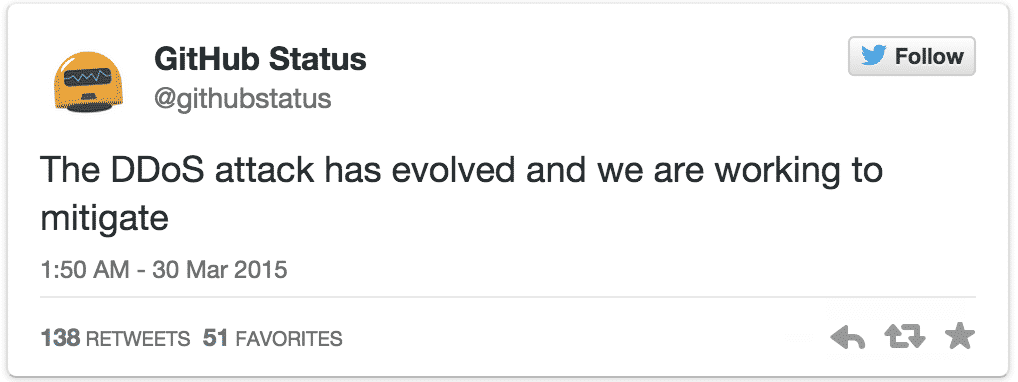
Now into its fifth day, the attack turned into something of a tug-of-war. Just as GitHub thought it had managed to wrestle back control of the site, a fresh wave was unleashed. The evolving attack is the largest in GitHub’s history and engineers “remain on high alert”.
The attackers have been using a variety of tactics over the course of the last few days, pursuing different areas of GitHub. The anti-censorship projects appear to have been key targets, and it included a project by Greatfire.org which aims to provide access to services and sites that are banned in China. Only last weekGreatFire.org suffered a DDoS attack of its own
On Friday, the GitHub status Twitter account was used to share some news about the attack:
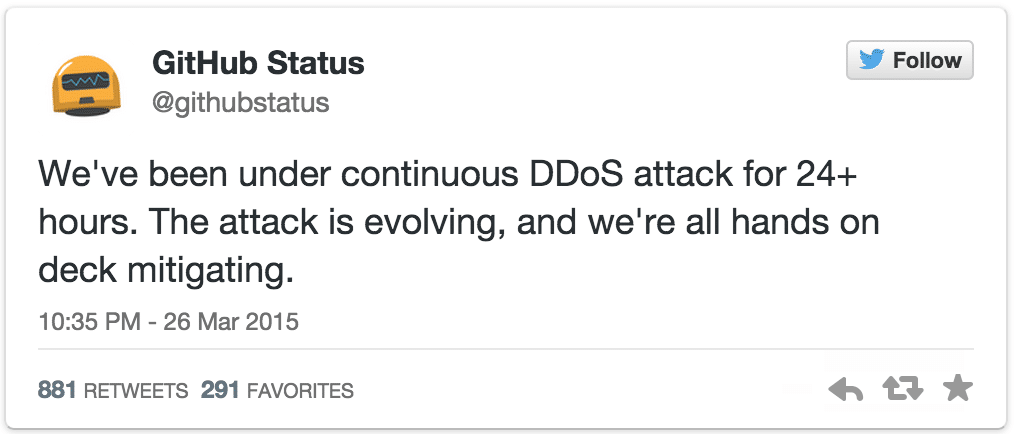
The battle against the attackers seemed to going GitHub’s way, but the onslaught intensified. A post on the GitHub blog explained:
The attack began around 2AM UTC on Thursday, March 26, and involves a wide combination of attack vectors. These include every vector we’ve seen in previous attacks as well as some sophisticated new techniques that use the web browsers of unsuspecting, uninvolved people to flood github.com with high levels of traffic. Based on reports we’ve received, we believe the intent of this attack is to convince us to remove a specific class of content.
At the moment, it would appear that the attacks originate from within China. As reported byPC World, one Chinese blogger has determined that advertising code may have been hijacked and used to pound GitHub with traffic. He found that when he visited Chinese websites, he started to notice JavaScript popups. Further investigation revealed that these were the result of trying to access the previously mentioned anti-censorship projects on GitHub. It looks as though someone has modified the ad tracking code used by Baidu — the Chinese search giant, comparable to Google — and used it to launch the DDoS attack.
That said, the attack has not yet been stopped in its tracks as it continues to adapt and change: